Tech
zvideo: The Emerging Frontier of Digital Viewing

Introduction
The digital world has never stood still. From grainy web clips in the early 2000s to ultra-high-definition streaming on demand, video consumption has evolved at an astonishing pace. Yet every few years, a new platform or concept appears that promises to reshape how we watch, share, and experience moving images. In recent discussions across tech communities and emerging media platforms, one name has quietly begun drawing attention: zvideo.
While not yet as universally recognized as mainstream video-sharing giants, zvideo represents something increasingly important in today’s media landscape—alternative, decentralized, and user-driven digital video ecosystems. Its presence signals a broader shift in how audiences value privacy, creative control, monetization freedom, and content authenticity.
Understanding zvideo requires more than a surface glance. It calls for examining the cultural forces behind its growth, the technology supporting it, and the reasons creators and viewers alike are gravitating toward newer, more flexible digital environments. This article explores zvideo in depth, unpacking its meaning, functionality, potential, and long-term implications for online video culture.
What Is zvideo
zvideo is a digital video platform concept and ecosystem that centers on flexible content distribution, community-driven engagement, and alternative media hosting models. Unlike traditional centralized video services, zvideo platforms often emphasize user autonomy, reduced content restrictions, and diversified monetization systems.
READ MORE: beit bart: The Quiet Rise of a Cultural Visionary in Motion
In practical terms, zvideo refers to online video-sharing environments designed to provide creators with greater control over their work while offering viewers a broader range of content types. These platforms may incorporate features such as decentralized hosting, encrypted streaming channels, independent subscription systems, or niche community curation.
The term zvideo has increasingly been associated with emerging digital spaces where traditional gatekeeping is minimized. In these environments, creators can experiment with formats that might otherwise struggle to find approval on highly regulated mainstream platforms. As digital media continues to fragment into specialized communities, zvideo represents that growing appetite for independence in online broadcasting.
The Evolution of Digital Video Platforms
To understand the importance of zvideo, it helps to trace the evolution of online video. Early internet video platforms were revolutionary but limited. Bandwidth constraints and basic compression technologies restricted quality and scale. As infrastructure improved, global video streaming became mainstream entertainment.
Large centralized platforms quickly dominated the space. They offered global reach, powerful recommendation systems, and monetization opportunities. However, with that dominance came strict content policies, algorithmic prioritization, and heavy reliance on advertising-driven revenue models.
Over time, creators began expressing frustration. Revenue unpredictability, sudden content removal, demonetization, and algorithm changes left many feeling vulnerable. Viewers, too, started questioning privacy policies and data usage practices.
zvideo emerged within this context—not necessarily as a single monolithic platform, but as a movement toward alternative video-sharing ecosystems. These systems respond directly to the concerns creators and viewers have developed over the past decade. They represent a new chapter in the digital video story, where flexibility and independence are increasingly valued.
Core Features That Define zvideo
The defining traits of zvideo platforms vary depending on implementation, but several recurring characteristics stand out.
One of the most significant is creator autonomy. In many zvideo environments, creators maintain ownership rights over their content and experience fewer arbitrary restrictions. This fosters experimentation, especially in educational, artistic, or specialized technical content that may not thrive under rigid moderation standards.
Another core feature is diversified monetization. Rather than relying solely on ad revenue, zvideo systems often incorporate direct subscriptions, microtransactions, community funding, or digital asset integration. This allows creators to build sustainable revenue streams without depending entirely on fluctuating advertising models.
Privacy and user control also distinguish zvideo. Some implementations use encryption protocols or decentralized hosting networks that reduce reliance on centralized servers. While not universally applied across all zvideo systems, this architectural flexibility appeals to users concerned about data surveillance.
Finally, niche community building is central to zvideo’s identity. Instead of broad mass appeal, many zvideo platforms cultivate tightly focused communities centered around shared interests, technical expertise, or creative subcultures.
Why Creators Are Exploring zvideo
Content creators today face both opportunity and uncertainty. The ability to reach global audiences is unprecedented, yet competition and platform dependency remain intense.
zvideo offers an appealing alternative for several reasons. First, it reduces reliance on unpredictable algorithms. Creators can interact more directly with their audience without constantly adjusting content style to satisfy automated ranking systems.
Second, revenue transparency is often clearer. In many zvideo models, income comes directly from viewers rather than third-party advertisers. This strengthens the creator-viewer relationship and builds trust.
Third, creative freedom plays a significant role. Artists working in experimental film, long-form discussion, independent journalism, or technical deep dives often find traditional platforms limiting. zvideo environments allow them to publish without fear of sudden removal due to automated moderation errors.
In an era where digital creators are building careers rather than casual hobbies, having alternative ecosystems like zvideo creates a healthier media economy.
Viewer Experience in the zvideo Ecosystem
While creators are central to the discussion, viewers benefit as well. The zvideo model often prioritizes quality engagement over mass consumption metrics.
Instead of endless scrolling through short, algorithmically curated clips, viewers may experience more intentional content discovery. Communities within zvideo platforms frequently operate on trust-based recommendations and thematic curation.
Privacy is another attraction. Some users are increasingly cautious about data tracking and behavioral profiling. zvideo platforms that incorporate decentralized hosting or encryption can provide a stronger sense of digital security.
Moreover, the absence of intrusive advertising enhances immersion. When monetization is subscription-based or community-supported, viewers often enjoy uninterrupted viewing experiences.
In short, zvideo reshapes not only how content is produced but how it is consumed.
Technological Foundations Behind zvideo
The rise of zvideo is closely linked to advances in technology. Cloud infrastructure, peer-to-peer networks, blockchain systems, and improved video compression algorithms have all contributed to its feasibility.
Decentralized hosting models reduce server bottlenecks and improve resilience. Instead of relying on a single centralized data center, distributed networks allow content to remain accessible even if one node fails.
Blockchain-based monetization systems in some zvideo environments enable transparent transactions. Smart contracts can automate revenue distribution, ensuring creators receive payment without intermediary delays.
Encryption technologies further enhance privacy and security. Secure streaming protocols protect both creators and viewers from unauthorized access or data misuse.
These technological innovations are not exclusive to zvideo, but they find meaningful application within its ecosystem.
Challenges and Limitations of zvideo
Despite its promise, zvideo is not without challenges. Infrastructure costs remain significant, especially for platforms that avoid advertising revenue. Sustainable funding models must balance accessibility with creator compensation.
Content moderation also presents complexity. While creative freedom is attractive, complete absence of oversight can lead to harmful or illegal material. Responsible zvideo platforms must strike a balance between openness and accountability.
Scalability poses another concern. As user bases grow, maintaining decentralized systems can become technically demanding. Performance optimization, bandwidth distribution, and security monitoring require ongoing investment.
Additionally, public awareness remains limited. Many users are deeply entrenched in established platforms and hesitant to migrate without compelling reasons.
These obstacles do not diminish zvideo’s relevance but highlight the work required to refine its model.
The Cultural Impact of zvideo
Beyond technical and economic considerations, zvideo reflects a broader cultural shift. Society is increasingly questioning centralized control in digital spaces. From finance to media, decentralization has become a recurring theme.
zvideo fits within this narrative by empowering individuals rather than corporations. It aligns with a growing desire for authenticity over algorithmic popularity.
Independent filmmakers, investigative journalists, educators, and niche hobbyists are finding spaces where their work can thrive without conforming to mass-market demands. This diversity enriches digital culture.
Moreover, zvideo encourages intentional engagement. When viewers subscribe directly to creators, the relationship feels more personal and meaningful. Content becomes less about chasing viral trends and more about delivering value to a committed audience.
In this way, zvideo contributes to a more thoughtful digital ecosystem.
The Future Outlook for zvideo
Predicting the future of digital platforms is always complex. However, certain trends suggest continued relevance for zvideo.
As audiences become more privacy-conscious, platforms offering data transparency will gain traction. As creators seek financial stability, direct support models will grow. As technological innovation lowers infrastructure barriers, decentralized systems will become more accessible.
zvideo may not replace mainstream video platforms entirely, but it does not need to. Its strength lies in complementing the existing landscape by offering alternatives.
Hybrid models may emerge, combining centralized convenience with decentralized flexibility. Established platforms could even integrate zvideo-inspired features to remain competitive.
What seems certain is that digital video consumption will continue evolving. And zvideo stands as a meaningful part of that evolution.
Conclusion
zvideo represents more than just another digital video platform concept. It symbolizes a response to the changing needs of creators and viewers in an increasingly complex online environment. By prioritizing autonomy, privacy, diversified monetization, and community-driven engagement, zvideo challenges the dominance of traditional centralized models.
Its growth reflects broader cultural movements toward decentralization and digital independence. While challenges remain—ranging from funding sustainability to responsible moderation—the underlying principles driving zvideo resonate strongly in today’s media landscape.
In a world where online spaces are often shaped by corporate interests and algorithmic control, zvideo offers an alternative path. It encourages creative freedom, meaningful viewer relationships, and technological innovation.
Whether it becomes a dominant force or remains a specialized ecosystem, zvideo has already sparked an important conversation about the future of digital video. And that conversation is far from over.
FAQs
What makes zvideo different from traditional video platforms?
zvideo differs primarily in its emphasis on creator autonomy, diversified monetization methods, and in some cases decentralized hosting. It often reduces reliance on advertising and algorithmic control, offering a more direct creator-viewer relationship.
Is zvideo a single platform or a broader concept?
zvideo is best understood as a broader ecosystem or concept encompassing alternative video-sharing environments rather than one singular globally dominant platform.
How do creators earn money on zvideo platforms?
Many zvideo models use subscription systems, community funding, direct payments, or blockchain-based transactions, allowing creators to earn revenue directly from viewers rather than relying solely on advertising.
Are zvideo platforms safe to use?
Safety depends on the specific platform implementation. Responsible zvideo environments incorporate moderation policies and security protocols to protect both creators and viewers.
Will zvideo replace mainstream video platforms?
It is unlikely to fully replace them. Instead, zvideo is positioned as a complementary alternative, offering different values and structures that appeal to creators and viewers seeking greater independence.

Tech
264.68.111.161 and the Limits of IPv4 Addressing Explained.!
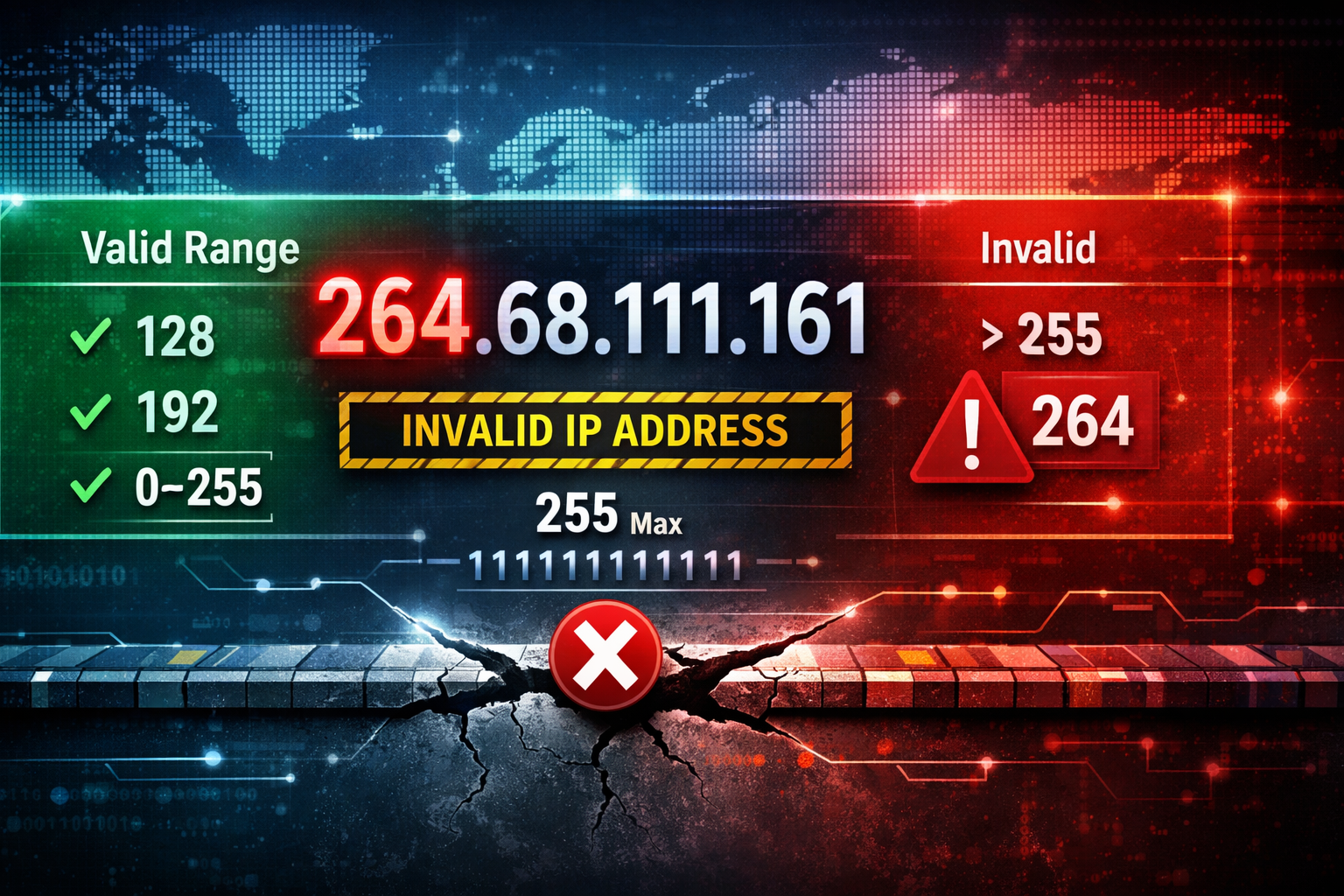
Introduction
At first glance, 264.68.111.161 looks like any other internet address. It follows the familiar dotted-decimal pattern most of us associate with IPv4: four numbers separated by periods. Yet beneath that ordinary appearance lies a subtle but important truth. Not every sequence that looks like an IP address is valid, and 264.68.111.161 is a perfect example of how technical boundaries quietly shape the digital world we rely on every day.
IP addresses are the invisible coordinates of the internet. They determine where data travels, how devices communicate, and how websites appear instantly when you type a domain into your browser. But those coordinates are governed by strict mathematical rules. When an address like 264.68.111.161 surfaces in logs, configurations, or discussions, it invites deeper questions. Is it real? Is it reachable? Could it ever function on the internet?
Understanding why 264.68.111.161 cannot exist as a legitimate IPv4 address opens a door into the architecture of the internet itself. It reveals how numerical systems, protocol design, and decades-old technical decisions still influence modern digital infrastructure. This is not just about one invalid number. It is about the boundaries that define the entire addressing system of the internet.
What Is 264.68.111.161
264.68.111.161 appears to be an IPv4 address written in dotted-decimal notation. IPv4 addresses consist of four numerical segments, each separated by a dot. These segments are called octets because each one represents eight bits of data. Since eight bits can represent numbers from 0 to 255, every valid IPv4 octet must fall within that range.
READ MORE: daylin ryder: Influence, Image, and Impact Unveiled in Media
The critical issue with 264.68.111.161 is found in its first segment. The number 264 exceeds the maximum allowed value of 255. That single numerical violation renders the entire address invalid within the IPv4 system. No router, operating system, or network device adhering to internet standards will recognize 264.68.111.161 as a legitimate address.
Despite its invalidity, sequences like 264.68.111.161 often appear in technical discussions, educational examples, test data, and even error logs. Sometimes they result from typographical mistakes. In other cases, they are deliberately constructed to illustrate the importance of IP address limits. While 264.68.111.161 cannot exist on the public internet, examining it helps clarify how IP addressing actually works.
The Mathematical Limits of IPv4
To understand why 264.68.111.161 fails, it helps to revisit the mathematics behind IPv4. The IPv4 protocol uses 32 bits to represent an address. Those 32 bits are divided into four groups of 8 bits each. Each group, when converted from binary to decimal, yields a value between 0 and 255.
Eight bits can produce 256 possible combinations, ranging from 00000000 to 11111111 in binary. When translated to decimal, that range becomes 0 to 255. There is no binary representation within eight bits that equals 264. To represent 264 in binary, you would need more than eight bits. That is the fundamental reason 264.68.111.161 cannot exist in IPv4.
This limitation is not arbitrary. It is deeply embedded in how IPv4 was designed in the early days of the internet. When the protocol was standardized, 32 bits were considered more than sufficient to handle global addressing needs. At the time, the scale of future internet expansion was difficult to imagine. Yet even with billions of possible combinations, IPv4’s boundaries are fixed. Any address exceeding those boundaries, including 264.68.111.161, simply falls outside the system.
Why 264.68.111.161 Cannot Exist on the Public Internet
In practical terms, no device can be assigned 264.68.111.161 as its IPv4 address. Network configuration tools validate entries against the 0–255 rule for each octet. If someone attempts to assign 264.68.111.161 manually, the system will reject it immediately.
Routers are designed to process packets based on valid IP headers. If a packet somehow contained 264.68.111.161 in its source or destination field, it would fail validation checks. Standard networking stacks conform to protocol specifications defined by long-established engineering standards. Those specifications make no allowance for octet values above 255.
Even more importantly, the global routing infrastructure relies on strict adherence to these rules. Internet backbone routers exchange route information based on valid address ranges. Since 264.68.111.161 does not fall within the IPv4 numerical space, it cannot be advertised, routed, or resolved anywhere in the world.
In other words, 264.68.111.161 is not just unused. It is structurally impossible within IPv4.
How Invalid IP Addresses Appear in Real-World Systems
Although 264.68.111.161 cannot function as a real IPv4 address, invalid addresses do appear in practical environments. They may show up in server logs, debugging outputs, database records, or user-submitted forms.
One common source is human error. A mistyped digit can push a valid address into invalid territory. For example, someone intending to type 164.68.111.161 might accidentally enter 264.68.111.161 instead. Without proper validation, that error could be stored in logs or passed through internal systems.
Another scenario involves automated testing. Developers sometimes generate intentionally invalid inputs to test how applications handle errors. Using an address like 264.68.111.161 allows engineers to confirm that validation routines are working correctly. If the system accepts it without complaint, that signals a flaw in input handling.
Cybersecurity analysis can also surface invalid addresses. Malformed packets, corrupted data streams, or malicious attempts to exploit poorly written software may include invalid IP values. In these cases, 264.68.111.161 becomes less of an address and more of a signal that something unusual is occurring.
Security and Validation Implications
The existence of invalid addresses like 264.68.111.161 underscores the importance of strict input validation in networked systems. When applications accept user-provided IP addresses, they must verify that each octet falls within the legal range. Failing to do so can open doors to unexpected behavior.
Improper validation may lead to software crashes, logging errors, or even vulnerabilities. For instance, if a system assumes that every dotted-decimal input is valid and attempts to convert 264.68.111.161 into binary without checks, it could trigger exceptions or memory-related issues.
In secure environments, input validation is layered. Systems verify not only that each octet is between 0 and 255 but also that the address conforms to context-specific rules. Some ranges are reserved for private networks. Others are designated for multicast or special-purpose use. Although 264.68.111.161 fails at the most basic numerical level, its existence in discussions highlights how much careful filtering happens behind the scenes.
Strong validation protects systems from malformed data, whether accidental or malicious. In that sense, 264.68.111.161 serves as a reminder of why defensive programming practices matter.
The Transition to IPv6 and Expanding Address Space
The limitations exposed by addresses like 264.68.111.161 also connect to a broader story: the eventual exhaustion of IPv4 address space. While 264.68.111.161 is invalid because it exceeds an octet boundary, IPv4 itself is limited to roughly 4.3 billion total addresses.
As the internet expanded globally, that pool proved insufficient. This led to the development and deployment of IPv6, a protocol using 128 bits instead of 32. IPv6 dramatically expands the address space, allowing an almost unimaginable number of unique addresses.
Even with IPv6, however, numerical rules remain strict. Every addressing system has boundaries defined by its bit structure. Just as 264.68.111.161 violates IPv4’s eight-bit limit, an IPv6 address that exceeds its designated structure would also be invalid. Protocol design always imposes limits.
The shift to IPv6 was not about correcting errors like 264.68.111.161. It was about scale. Yet both topics share a common foundation: the mathematical architecture underlying network communication.
Misconceptions About “Unused” Versus “Invalid”
A common misunderstanding is the belief that any unassigned address is simply “unused” rather than invalid. There is an important difference. Many IPv4 addresses remain unassigned or reserved at any given time. These are valid addresses that are not currently in active use.
By contrast, 264.68.111.161 is not unused. It is invalid. It falls outside the permissible range entirely. This distinction matters in technical discussions. Unused addresses can potentially be allocated in the future. Invalid addresses can never be allocated because they do not conform to protocol rules.
Confusing these concepts can lead to flawed assumptions in network planning or software development. Recognizing that 264.68.111.161 is structurally impossible rather than merely inactive clarifies the importance of respecting protocol boundaries.
The Educational Value of Impossible Addresses
There is surprising educational value in examining something that cannot exist. 264.68.111.161 is a teaching tool disguised as a number. It illustrates how binary representation translates into decimal form. It highlights why eight bits stop at 255. It demonstrates how protocol standards enforce consistency across the globe.
When students first learn about IP addressing, seeing an invalid example can make the rules more concrete. Instead of memorizing limits abstractly, they see the consequences of exceeding them. The number 264 becomes more than a statistic. It becomes a boundary line.
Engineers, too, benefit from revisiting fundamentals. In a world where high-level abstractions often hide low-level details, remembering why 264.68.111.161 cannot exist reconnects us to the foundational logic of networking.
Conclusion
264.68.111.161 may look like an ordinary IPv4 address, but it represents the precise boundaries that define internet communication. Its invalid first octet exposes the strict 0–255 rule rooted in eight-bit binary structure. That single numerical overflow disqualifies it from existing anywhere within the IPv4 system.
Exploring 264.68.111.161 reveals more than a simple formatting mistake. It uncovers the mathematical design of IPv4, the necessity of validation, the structure of global routing, and the broader evolution toward IPv6. It clarifies the difference between unused and impossible addresses. It also reminds us that every digital system operates within carefully defined constraints.
In the end, 264.68.111.161 is not a real address. It will never route traffic, host a server, or identify a device. Yet by understanding why it cannot, we gain a deeper appreciation for how the internet truly works.
FAQs
What makes 264.68.111.161 invalid as an IPv4 address?
264.68.111.161 is invalid because the first octet, 264, exceeds the maximum allowed value of 255. IPv4 octets are limited to numbers between 0 and 255 due to their eight-bit structure.
Can 264.68.111.161 be used in any private or experimental network?
No. Even in private or experimental environments, IPv4 rules remain the same. Since 264.68.111.161 violates the 0–255 range requirement, it cannot function as a valid IPv4 address anywhere.
Why do addresses like 264.68.111.161 sometimes appear in logs?
They often appear due to typographical errors, corrupted data, or deliberate testing of input validation systems. Developers sometimes use invalid addresses to ensure that software properly rejects them.
Is 264.68.111.161 considered unused or unassigned?
It is neither unused nor unassigned. It is invalid. Unlike legitimate but unallocated addresses, 264.68.111.161 falls outside the numerical limits defined by IPv4.
Does IPv6 remove limitations like the one affecting 264.68.111.161?
IPv6 greatly expands the available address space, but it still has strict structural rules. Just as 264.68.111.161 violates IPv4 boundaries, an improperly formatted IPv6 address would also be invalid under its own specifications.
-

 Biography2 days ago
Biography2 days agobeit bart: The Quiet Rise of a Cultural Visionary in Motion!
-

 Blogs12 hours ago
Blogs12 hours agoThe Cultural Rise of doujen moe in Fan Art Worlds
-

 Business2 days ago
Business2 days agomariano iduba: Architect of Purposeful Change Today Globally
-

 Business12 hours ago
Business12 hours agogoldzeus Redefining Digital Gold Ownership in Modern Finance
-

 Blogs12 hours ago
Blogs12 hours agodaylin ryder: Influence, Image, and Impact Unveiled in Media
-

 Blogs13 hours ago
Blogs13 hours agofascisterne: Ideologi, Magt og Europas Mørke Arv
-

 Entertainment2 days ago
Entertainment2 days agoreadmymanga com: The Hidden World Behind Manga Access
-

 Tech8 hours ago
Tech8 hours ago264.68.111.161 and the Limits of IPv4 Addressing Explained.!